Ransomware froze more cities in 2019. Next year is a toss-up
More than 70 state and local governments across the US suffered ransomware attacks in 2019.
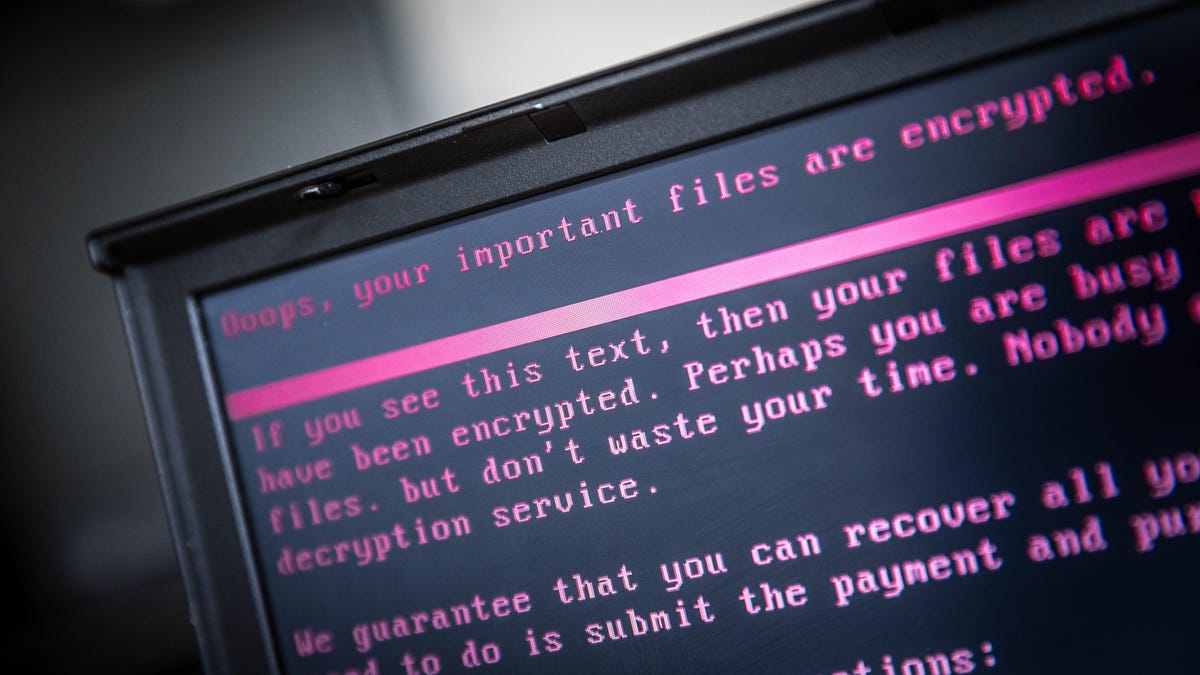
Ransomware attacks against local governments spiked in 2019, researchers found.
When Hurricane Sandy hit the East Coast in 2012, it caused a power outage affecting nearly 8 million homes and workplaces, including the office of Manhattan District Attorney Cyrus R. Vance Jr.
The building's computers couldn't turn on, but police were still making arrests, and his office still needed to prepare cases for trial. So his staff turned to pen and paper, writing out criminal complaints by hand and, on some nights, by candlelight.
The natural disaster cost New York City about $19 billion. What could be equally devastating for the city? According to Vance, the scourge of ransomware.
Ransomware is malicious software that spreads quickly across computer networks and encrypts them, holding sensitive documents hostage until victims decide to pay the hackers. If a ransomware attack successfully struck the Manhattan DA's office, Vance said the consequences would be "cataclysmic."
"We had something that presaged for us what a ransomware attack might look like," Vance said. "When Hurricane Sandy came in, it shut down all electricity in the office. We had no power. That's analogous."
Hackers used to attack the average person with ransomware but have discovered that governments are much more willing to pay up because they hold more sensitive data and inherently have deeper pockets. While Vance's office has been fortunate enough to avoid a ransomware attack so far, many government entities across the US have fallen victim to such attacks.
Attacks spiked this year, with more than 70 state and local governments hit with ransomware, according to IT security company Barracuda Networks. The malware has also hit hospitals, businesses and universities, but governments have become a prime target. Barracuda Networks found that two-thirds of all known 2019 ransomware attacks in the US targeted governments.
"These government organizations are not always well-equipped on cybersecurity concerns, which makes them easy targets," said Kevin Latimore, enterprise malware removal specialist for security software provider Malwarebytes. "Not only do they have potential to pay, but they are a soft target."
Local governments are also more frequently opting to pay the ransomware rather than rebuild their systems. After seeing Atlanta spend $2.6 million to restore its systems rather than pay the $52,000 ransom, many officials have decided that it's cheaper to pay the hackers.
Such payments have convinced hackers to target more governments and ramp up their demands, according to security experts. To stave off the increasing threat of ransomware attacks, government officials are turning to cybersecurity companies for help, as the federal government also looks to safeguard state and local governments from major hacks. If government continue to pay, though, experts warn that ransomware will continue to grow in 2020.
"If you feed the seagulls, what's going to happen?" Latimore said. "Not only will the hackers we know about continue, but there will also be others that are attracted to ransomware if it continues to be a source of income."
Feeding the seagulls
Ransomware attacks jumped this year after security experts first saw an outbreak in 2017 through WannaCry and NotPetya. The former was a North Korean attack that quickly spread throughout networks in Europe, locking up computers in hospitals, airports and universities. The latter was an attack from Russia on Ukrainian software that spread to hundreds of businesses, causing the most destructive cyberattack in history.
NotPetya cost shipping giant Maersk up to $300 million in lost revenue. The attacks had devastating effects by locking up computer systems, in some cases even forcing hospitals to close permanently.
By the end of 2017, ransomware attacks had slowed down. And at the beginning of 2018, experts believed that hackers were moving on from these types of campaigns. People were backing up their files more often, which at the time served as a functioning antidote to the attacks. Even if ransomware was encrypting people's files, they had backups to rely on.
And then the hackers got smarter.
In this year's ransomware cases, the malware lies dormant on people's networks and sets itself up to cause as much damage as possible before triggering the attack. That often means blowing up the backups.
"Before they drop their encryption, they look to cause maximum pain," Latimore said. "They destroy backups, which leaves many who have that plan to completely start from scratch."
The Ryuk ransomware, one of the most active campaigns in 2019, hit more than 500 schools. Security researchers believe the Ryuk ransomware is named after the god of death in the anime Death Note.
The Ryuk ransomware strain waits until it spreads across a computer's network before launching the attack, researchers say. This is the note an affected victim would see.
Latimore said the malware was efficient at finding backups and destroying them before launching the full attack.
With little-to-no options left for recovery, local governments started paying the hackers. A ProPublica report in August found that insurance companies helping pay ransoms were essentially encouraging hackers to continue these attacks for profit.
Insurance giant AIG reported in July that ransomware was its second leading cause of claims in 2018 and expected an increase for 2019. While the number of attacks had actually decreased, AIG explained that such attacks have become more costly as the targets have become more specific, particularly local governments with deep pockets and shallow security measures.
As more governments pay, hacker demands increase.
"What we're seeing is that the ransoms are growing steeper," IBM X-Force Vice President Wendi Whitmore said. "Atlanta was asked for $50,000. And then a city much smaller than Atlanta was asked for $450,000."
In the span of one week this summer, two Florida cities paid a combined $1.06 million to hackers over ransomware attacks. In New Bedford, Massachusetts, hackers demanded a $5.3 million ransom this summer and rejected the city's offer of $400,000 to restore its systems.
In response to these massive ransom demands, a coalition of 227 US mayors vowed this summer not to pay hackers over ransomware attacks. But rather than wait for that day to come and put those vows to the test, many governments have decided to shore up their protections against ransomware attacks.
Guarding against ransomware
As the largest city in the US, New York is constantly facing threats of a potential cyberattack. But it wasn't until 2017 when Manhattan's district attorney realized that his department would be helpless if it were hit by ransomware.
Vance isn't the only city official who's had that realization. The city's emergency responders, including the police and fire departments, have started training for cyberattacks, NYC Chief Information Security Officer Geoff Brown said at the Aspen Institute Cyber Summit in October.
The trainings are important to make sure that government officials aren't caught flat-footed if the city ever gets attacked.
"Sometimes people think this is a purely technical exercise, but important decisions need to be made. And that means that decision makers need to think about them before they're in the midst of an actual crisis," Brown said at the summit.
In July, NYC officials took part in IBM's "Cyber Range" exercise in Massachusetts, where the company set up a simulation to show them what it'd be like if the city suffered a ransomware attack.
The company had worked with NYC officials for about two to three months to figure out where the city's weaknesses were to set up the simulation, IBM's Whitmore said. Cities like Los Angeles have also taken part in the simulation, she said.
The goal is for government officials to learn what a ransomware attack looks like and how to respond to it.
"Our simulations are extremely realistic, we have a variety that we can use, and some are completely customized for the organization," Whitmore said.
For Vance, the experience was eye-opening.
He's now involved in a group chat on the encrypted app Signal with 17 others involved with hospitals, police, public transportation and mobile service providers. The group is constantly sharing information on potential cyberattacks and how to defend themselves from these threats, he said.
The office has also taken extra security measures and precautions to make sure it can withstand a ransomware attack.
"Because of the ransomware attacks recently, we've now made decisions to back up more frequently," said Kenn Kern, the district attorney office's chief information officer. The office used to back up all its files once a day at 3 a.m., but now does it twice a day and is considering doing it more frequently, Kern said.
"We have to have a duplicate copy of basically everything that exists for us as an organization," he said.
Small town woes
Not everybody has massive resources like New York or access to a cybersecurity simulation from IBM. Outside of cities like Baltimore and Atlanta, it's often towns or small businesses that have been ensnared by ransomware attacks.
Matthew Travis, deputy director of the Department of Homeland Security's Cybersecurity and Infrastructure Security Agency, met with governors, mayors and state lawmakers in the summer of 2018. They all had one concern.
"As those officials came up to me, they didn't want to talk about elections, they didn't want to talk about industrial control systems or utilities," Travis said at the Aspen Institute's Cyber Summit. "They didn't want to talk about federal networks or some of the other cybersecurity problems that exist. They wanted to talk about ransomware."
Security researchers from Malwarebytes saw a spike in the number of ransomware incidents in 2019 compared with the previous year.
Latimore said Malwarebytes has been working with towns to deal with ransomware attacks. In August, the company detailed how it helped prevent ransomware from taking over a school district with about 3,200 students in the East Irondequoit Central School District in western New York.
The school district had 1,400 computers infected with ransomware, and it was spreading fast.
"We started getting Help Desk calls that devices had blue screened and quickly realized we had a significant issue," Joseph Sutorius, the school district's chief information officer, said in Malwarebyte's case study.
Latimore said he was able to find the trojans and completely remove them before the attack spread throughout the network and encrypted all the school district's files.
While that school district was fortunate enough to avoid a major attack, the outlook for local and state governments isn't great for 2020. Still, government officials and lawmakers have at least recognized the threat of ransomware.
This year, the House and the Senate approved versions of a bill that would allow the DHS to invest in resources to help states and cities deal with ransomware attacks. In September, the Senate sent the bill back to the House with changes.
"As cyber threats become increasingly common, it is crucial that everyone from the federal government to local governments like Strafford County have the resources and support that they need to strengthen their cybersecurity," Sen. Maggie Hassan, a Democrat from New Hampshire and a bill co-sponsor, said in a statement.
On Wednesday, the senators had a classified DHS briefing on ransomware, calling it a "growing threat," but something local governments could protect themselves from.
"The continued prevalence of ransomware should really capture our attention. It's costly, devastatingly high-impact, growing, and, in most cases, easily preventable with basic responsible cybersecurity practices," Sen. Mark Warner and Sen. Cory Gardner, co-chairs of the Senate Cybersecurity Caucus, said in a statement. "While often viewed as basic digital extortion, ransomware has had materially adverse impacts on markets, social services like education, water, and power, and on healthcare delivery, as we have seen in a number of states and municipalities across the United States."
Security experts expect ransomware attacks against local governments to ramp up in 2020. But government officials hope that if they can properly protect cities and stop paying the hackers, ransomware will eventually die off.
The Homeland Security Department's Cybersecurity and Infrastructure Security Agency (CISA) hopes to provide security measures for everyone, not just major cities that can pay for these protections.
"Large companies, large municipalities can make those investments," CISA's Travis said. "What we're trying at CISA is create toolkits for more rural communities, more rural school districts, small businesses that may not do all those things in terms of cyber essentials."

